The evolution of Decentralized Finance (DeFi) has been transformative, introducing us to numerous groundbreaking concepts such as MakerDAO, Compound Finance, and Uniswap.1 The ecosystem has continuously thrived and expanded, owing to the growing adoption of protocols and the innovation they foster. As a part of this rapidly evolving ecosystem, 2020 introduced a phenomenon, the 'DeFi Summer', and several new concepts, such as liquidity mining or farming, surged, adding further depth and complexity to the landscape. More recently, Liquid Staking Derivatives2 Finance3 (LSDfi) has surfaced, showcasing the limitless potential of DeFi. These developments have paved the way for an essential tool within the DeFi space that efficiently leverages and optimizes these varied strategies - the concept of 'Vaults'.
What are Vaults?4
Vaults are smart contracts that utilize particular strategies5 for deploying capital. Most vaults leverage automation to consistently invest and reinvest the assets deposited, facilitating substantial compound interest generation. Users can avoid innumerable transactions, associated gas costs, and time investment by employing a vault to compound interest. Instead of carrying out repetitive manual tasks such as harvesting rewards, purchasing more tokens, and perpetually reinvesting, a vault automates these processes efficiently and frequently.
Contrary to what the term 'Vault' might imply, user funds are never restricted or unable to withdraw within most DeFi vaults. Users usually retain the ability to redeem the underlying assets from a vault at any given time. It's also important to note that the protocols/developers who usually deploy the vault do not possess ownership over user assets staked within such vaults. Nevertheless, vaults are considered medium to long-term asset storage to benefit from the compounding interest. After users deposit tokens to a vault, they receive vault-specific tokens representing their share.
From a front-end point of view, most protocols display the annual percentage yield (APY), which accounts for the impact of frequent compounding, unlike the annual percentage rate (APR), for each vault. Additionally, the aggregate sum invested in a vault by all users, referred to as the total value locked (TVL), is usually available as most information about the vault's strategy.
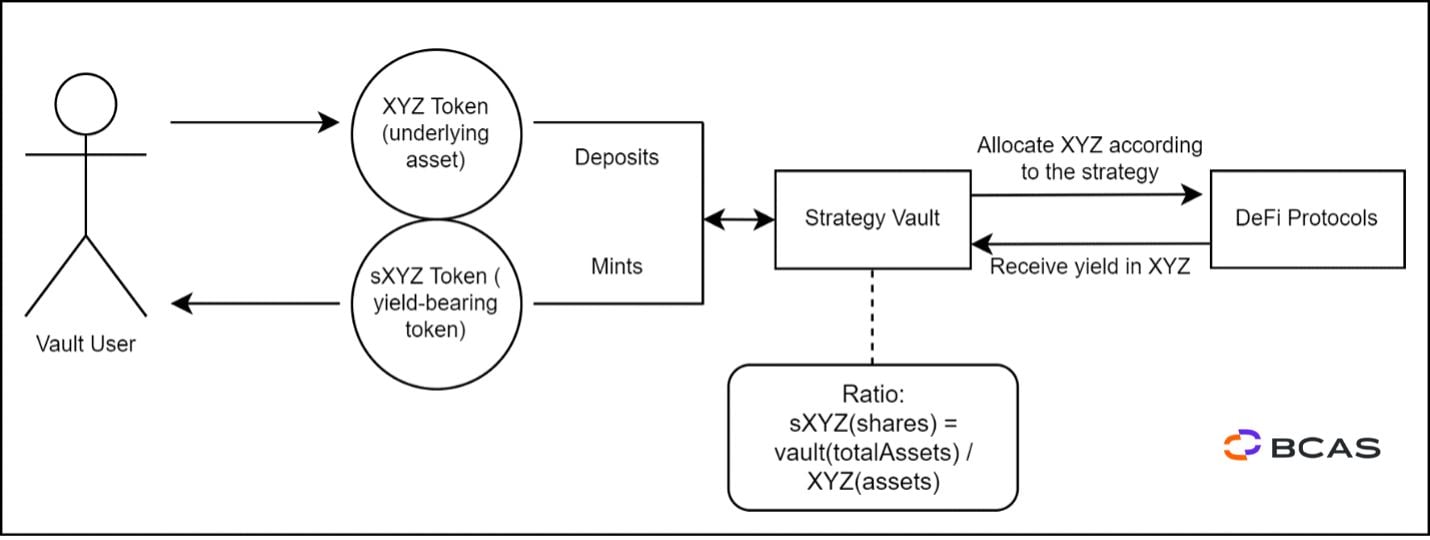 Figure 1 – Vault Logic Example
Figure 1 – Vault Logic Example
In the example above, the vault mints tokens representing the assets deposited by the user. In Figure 1, the Vault User receives the sXYZ6, an interest-bearing, tokenized proof of deposit into the Strategy Vault. The Vaults automatically allocates XYZ according to the defined strategy, generating more deposited assets in simple or compounded interest. As a result, sXYZ increase in value relative to their corresponding vault asset. The number of minted sXYZ remains constant while the XYZ amount that can be redeemed increases. Therefore, sXYZ will not have a 1:1 ratio with the initially deposited XYZ.
The user may redeem sXYZ for XYZ at any time in proportion to the capital deposited plus the yield generated.
The following chapter shall delve into a more comprehensive insight into the practical operations of vaults. It's important to note that there may be an abundance of strategy vault types; however, for ease of understanding, we will only concentrate on the primary use cases for such vaults.
Vaults Use-cases
Simple Strategy Vaults
Yield-bearing vaults were originally designed as an effective aggregation tool for lending. These vaults were designed for users to deposit a specific crypto-asset, and the vault would deploy and shift capital between different platforms to ensure that users always obtain the highest interest rates.
For example, a vault could interact with yield-generating protocols such as Compound, Aave, Curve, and Convex and deploy the capital towards the protocol promising the highest annual percentage yield.
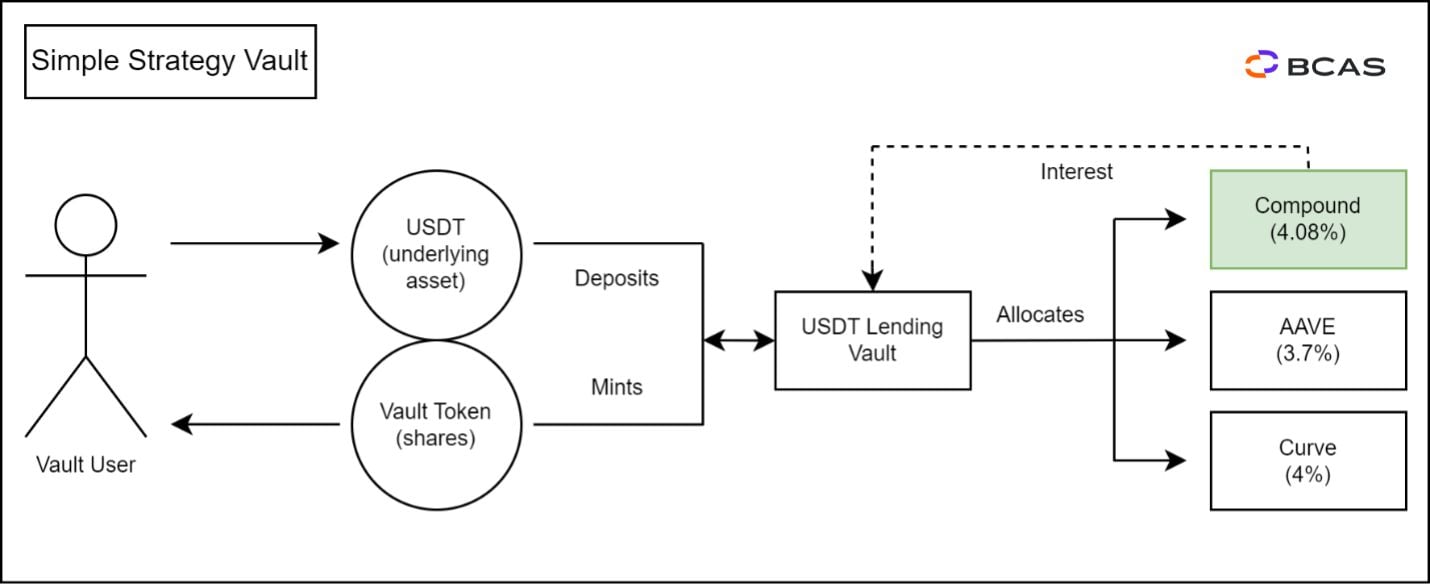 Figure 2 - Simple Strategy Vault Example
Figure 2 - Simple Strategy Vault Example
As illustrated in Figure 2, the Vault User deposits USDT and is subsequently issued a corresponding Vault Token. Concurrently, the USDT Lending Vault systematically directs the USDT to the most profitable yield available in the DeFi space, which in this particular instance, is the Compound Protocol. By allocating the USDT in the Compound Protocol, the Vault earns an APY of 4.08% on the USDT. As a result, the inherent value of the Vault Token experiences an increase in value owing to the accumulation of USDT.
This type of strategy vaults may also be applied to LSDfi, where instead of allocating capital to lending protocols, the vault delegates the assets to a node to benefit from the rewards provided for securing the network.
Yield Farming Vaults
Yield farming or liquidity mining, is a mechanism that rewards users for supplying liquidity to enhance the value of a dApp's ecosystem. Yield farmers (those making deposits) receive rewards proportional to their deposit amount, paid in the application's native token. This results in a higher APY for the user on their supplied liquidity. The crypto-asset rewards from yield farming add to the protocol's intrinsic revenue streams, such as trading fees within a decentralized exchange or interest from lending in a decentralized money market7.
Yield Farming Vaults, or Yield Optimizers, are vaults designed to automate and enhance the yield farming process. These vaults accumulate and automatically reinvest the earnings generated from yield farming. When users deposit their assets into a Yield Farming Vault, the vault utilizes these assets to provide liquidity to DeFi protocols and earns rewards, which are fees and the protocol's native crypto-asset. The protocol's native crypto-asset is subsequently sold to acquire more of the underlying asset.
If the protocol allows, the user may deposit a single crypto-asset from the pair required to provide liquidity to the pool of such crypto-assets and will perform a routing to swap half of the deposited crypto-asset for the pair. Afterwards, it shall build a liquidity position using both crypto-assets on a 50/50 market value ratio and receive a liquidity pool (LP) crypto-asset representing the deposit on the LP.
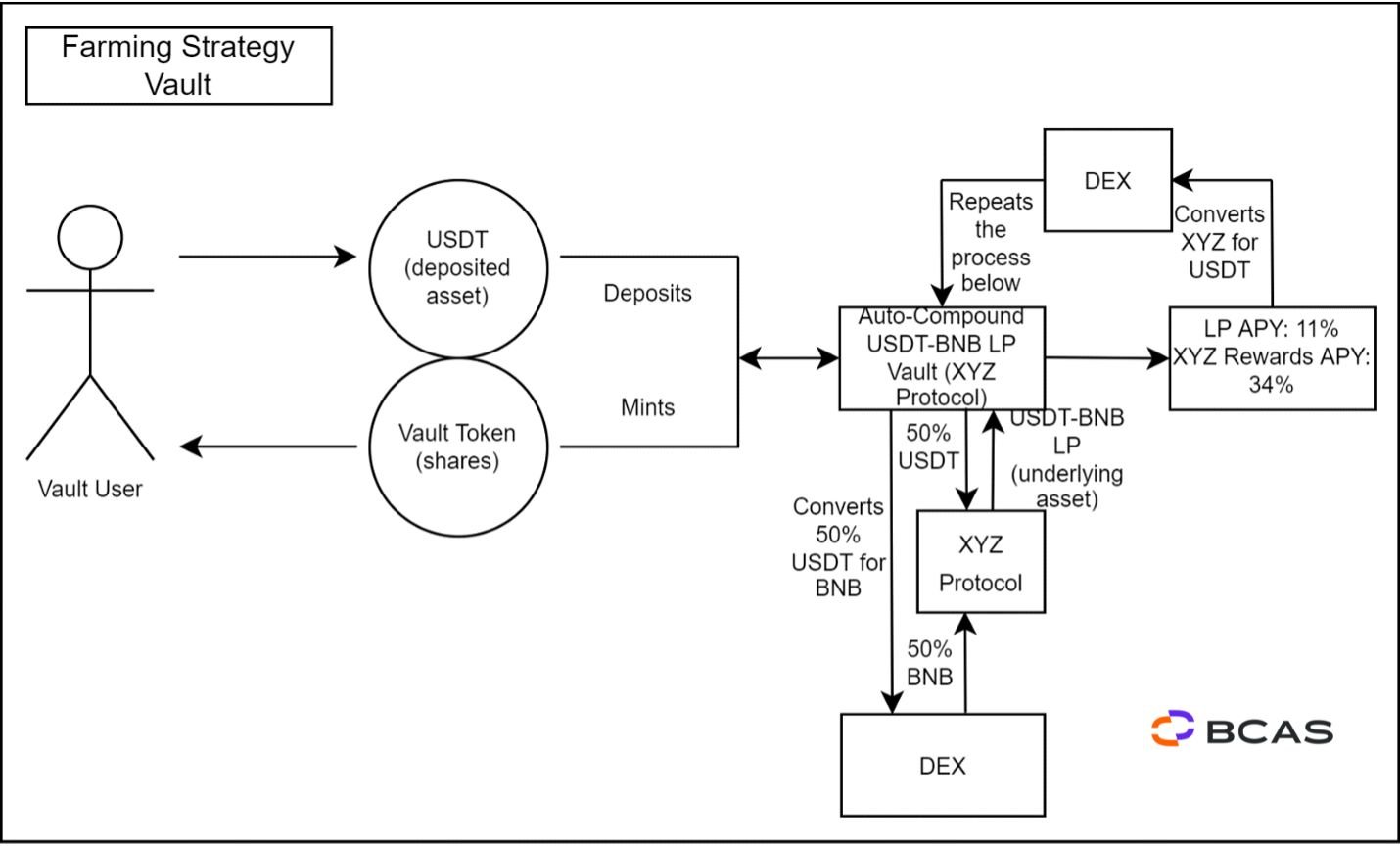 Figure 3 - Yield Farming Vault Example
Figure 3 - Yield Farming Vault Example
In our example, the Vault user only deposits USDT. The protocol automatically swaps half of the USDT for BNB and provides liquidity in the USDT-BNB LP, receiving USDT-BNB LP. Afterwards, the vault deposits the user's USDT-BNB LP crypto-asset into the XYZ Protocol, accumulating the LP fees and the protocols' governance/reward crypto-asset. XYZ, the protocol governance token, is exchanged for additional underlying assets to increase the crypto-assets holding in the liquidity pool. To round off the compounding cycle, the newly obtained USDT-BNB is reintroduced to the farm and prepped for the upcoming earning event. The vault's users collectively bear the transaction expenses incurred during this process.
Complex Strategy Vaults
These vaults offer the ability to apply multiple strategies concurrently. This amplifies the overall versatility in capital management, allowing for efficient handling of resources under varying market conditions.
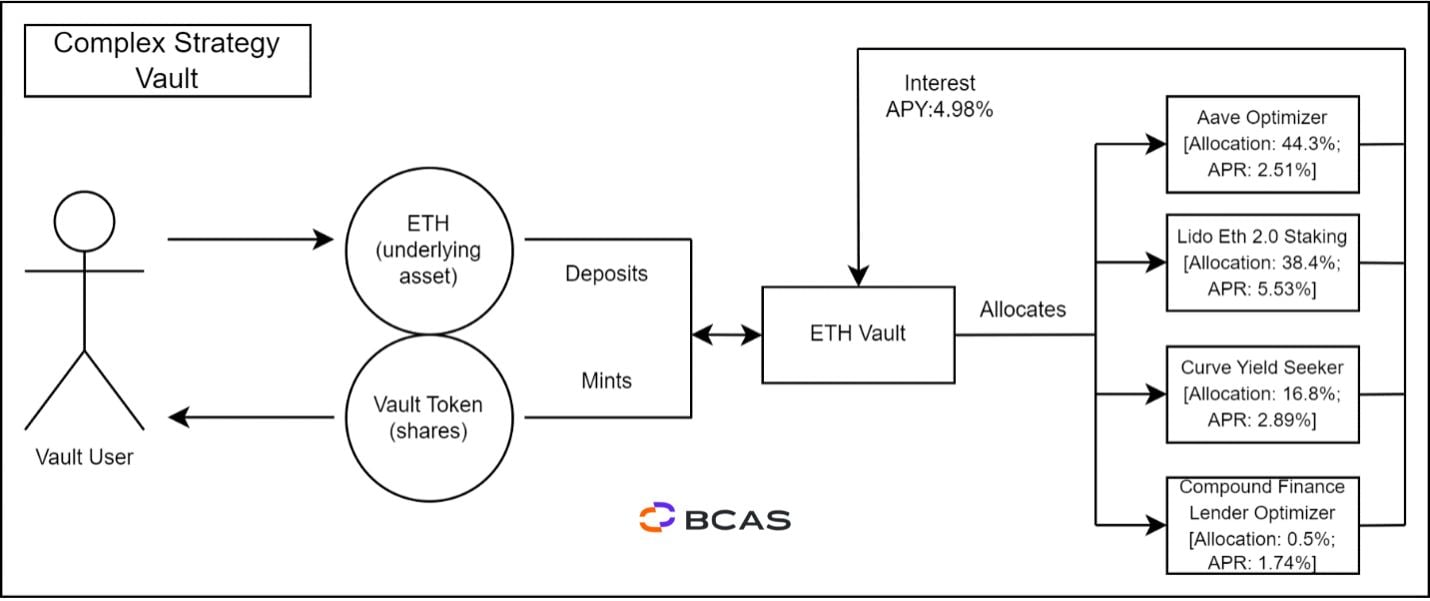
Figure 4 - Complex Strategy Vault Example
The example provided in Figure 4 was based on the yearn.finance v2 ETH vault8. In this scenario, a user contributes ETH9 to the vault, which distributes the capital among various protocols, following the strategies set within the vault. The allocation could be for yield farming purposes or to accrue interest through capital lending. At present, this vault takes advantage of three liquidity mining allocations and a straightforward strategy of staking ETH on an LSDfi protocol, detailed as follows:
- Aave Optimizer: Supplies 44.3% of the vault's ETH to AAVE v3 and v2 to generate interest and earn rewards. Earned tokens are harvested and sold for more WETH, which is deposited back into the strategy.
- Lido Eth 2.0 Staking: Stakes 38.4% of the vault's ETH on Lido.fi to mint stETH, accumulating ETH 2.0 staking rewards. This strategy will buy stETH off the market if it is cheaper than staking.
- Curve Yield Seeker: Supplies 16.86% of the vault's ETH to Curve Finance to earn CRV. Earned tokens are harvested and sold for more ETH, which is deposited back into the strategy. Strategy automatically switches to the most profitable Curve pool.
- Compound Finance Lender Optimizer: Supplies 0.5% of the ETH to Compound Finance to generate interest and earn COMP. Earned tokens are harvested and sold for more ETH, which is deposited back into the strategy.
Through the implementation of its strategies, the vault effectively allocates capital to yield a net APY of 5.03%10.
ERC-4626: The Tokenized Vault Standard
The Ethereum community has embraced a multitude of standards, which serve to retain interoperability among projects across varied implementations. These standards are also instrumental in ensuring that smart contracts and decentralized applications remain composable11.
As described in this article, the strategy vaults became a backbone for decentralized finance applications, where in one way or another, some Vault is deployed whenever an automated strategy applies to the capital deposited. As a result, the ERC-4626 interface was born: a new standard was required to lower the integration effort and allow developers to focus on creating more consistent and robust implementation patterns. ERC-4626 is a normative measure to optimize and standardize the technical variables associated with yield-bearing vaults12. It establishes a uniform API for tokenized yield-bearing vaults, which indicate the shares associated with an underlying ERC-20 token. In addition, ERC-4626 defines an optional extension for the tokenized vaults that use ERC-20, introducing rudimentary functionalities such as depositing and withdrawing tokens and balance inquiry13.
All ERC-4626 tokenized vaults must implement ERC-20 to represent shares. However, if a vault is deemed non-transferrable, it may revert on calls to transfer or transferFrom. For the scope of this article, we shall focus on two main features/variables/definitions of the ERC-4626, the "asset" and the "share"14:
- The "asset" refers to the underlying token that the vault manages and must adhere to the ERC-20 standard.
- The "share"15 is the vault's token, representing a claim of ownership of a portion of the underlying assets held in the vault. It maintains a ratio of underlying assets exchanged during minting, depositing, withdrawing, or redeeming.
These concepts were presented in the introduction of the Section "What are Vaults?". For convenience's sake, we shall provide an example to understand the ratio of the "assets" to the "shares".
- Alice and Bob each deposited 10,000 USDT into the Simple Strategy Vault simultaneously. For the sake of simplicity, no interest was accumulated between their deposits, and both users received newly minted 10,000 sUSDT, the ERC-4626 token representative of their deposit.
- The Simple Strategy Vault has an APY of 120%, without any auto-compounding feature, and no fees are charged. One month has elapsed without any additional deposits. Currently, the total assets of the Simple Vault should be equal to the initial capital deposited (10,000 x 2) plus the accrued interest (initial capital deposited x annual percentage yield/12), amounting to a total of 22,000 USDT (20,000+2,000).
- The 20,000 sUSDT now corresponds to 22,000 USDT, indicating the new ratio of 1 sUSDT to 1.1 USDTs, calculated as totalAssets/shares.
- Intrigued by Alice and Bob's experience with the Simple Strategy Vault, Charlie also decided to deposit 10,000 USDT. However, given the change in the deposit-to-mint ratio, Charlie receives approximately 9,090.91 sUSDTs to maintain the balance between assets and shares.
- Consequently, the Simple Strategy Vault has minted 29,090.91 sUSDTs, representing the 32,000 USDTs deposited, adhering to an sUSDT price of 1.1 USDT.
ERC-4626 and Markets in Crypto-Assets Regulation (MiCA)
The MiCA establishes a unified regulatory environment across the European Union to safeguard investors through enhanced transparency measures and by implementing a comprehensive legal structure for issuers and service providers, which includes compliance with anti-money laundering regulations. The newly introduced regulation defines crypto-assets, asset-referenced tokens, electronic-money tokens and utility tokens. They are distinguished from one another and subject to different requirements depending on the risk they entail. They are classified as whether the crypto-asset seeks to stabilize its value by reference to other assets, should it be an official currency, any other value or right or no reference at all16.
MiCA defines a "crypto-asset" as "a digital representation of a value or a right which may be transferred and stored electronically, using distributed ledger technology(DLT) or similar technology"17.
This extensive interpretation of a "crypto-asset" underscores the regulators' intent to capture as many digital assets within its regulatory purview as possible. It will likely lead to a significant expansion of the types of digital assets that fall within the scope of regulated entities under the EU's jurisdiction.
In light of the examples provided that pertain to vaults utilizing the ERC-4626 interface in conjunction with the MiCA approach to crypto-assets, we have identified four primary factors that must be considered to classify the ERC-4626 shares. These considerations are as follows18:
1st - A Digital Representation of Value on a DLT
While "representation of value" may seem unclear, further clarification is provided in the preamble of MiCA. It states that a "representation of value" includes an "external, non-intrinsic value attributed to a crypto-asset by the parties concerned or market participants." This value is subjective and is based only on the interest of the purchaser of the crypto-asset. Therefore, any crypto-asset that is transferable and has any value between two parties falls under the scope of MiCA.
2nd - Transferability, the Relevant Exclusion19
Non-transferrable digital assets do not meet the criteria to be classified as crypto-assets. Hence, such digital assets, which are exclusively accepted by the issuer or offeror and technically non-transferable to other holders, should be excluded from MiCA's purview. The smart contract must have a technical restriction in place to prevent the execution of any transfer function.
Contraintuictively, a non-transferable ERC-20 should still have the transfer and transferFrom functions to follow the ERC-20 standard. Not including such functions in the smart contract would render the crypto-asset a non-ERC-20 since it would not comply with the standard. This is highly relevant since, in order to follow the ERC-4626 standard, implementing the ERC-20 standard to represent the shares is mandatory. Therefore, the consensual solution for non-transferable ERC-20 is to revert any call to transfer or transferfrom.
However, it is insufficient for the ERC-20 implementation of shares on the ERC-4626 to revert on calls to transfer or transferFrom to be considered non-transferable. The non-transferability must be permanent, without any conditions to become transferable, such as USDC, where transfers may be temporarily suspended and reinstated20, or upgradeable.
What are Upgradeable Smart Contracts?21
Smart contracts, once deployed to a blockchain, are permanent, immutable and unmodifiable22. However, a dApp may be designed to create a complex system with multiple smart contracts operating together. As a result, swapping one smart contract out for another is possible without changing how the end-user interacts with the dApp.
The prevalent method for updating smart contracts involves utilizing the "Proxy Pattern" software design model. A proxy functions as an intermediary layer that directs incoming interactions from the user-facing front end to the appropriate smart contract on the system's back end. As a smart contract, a proxy possesses a permanent Ethereum contract address. The proxy allows for the substitution of different smart contracts within the system, with the proxy smart contract merely needing to be updated with the address of the newly launched smart contract. The end-users of the dApp interact directly with the proxy and only indirectly with the other smart contracts facilitated through the proxy.
In smart contract development, the Proxy Pattern is accomplished using two main components:
- The Proxy Smart Contract;
- The Implementation Contract.
While several prevalent versions of the proxy pattern exist, for clarity, our focus will be primarily on comprehending the concept of upgradeability via proxy from a broad perspective23.
The proxy contract has its logic and storage, where data is stored permanently on the blockchain. The proxy contract employs storage variables to monitor the addresses of the various other smart contracts that constitute the dApp. Through this process, it can reroute transactions and call the appropriate smart contract via the delegatecall message.
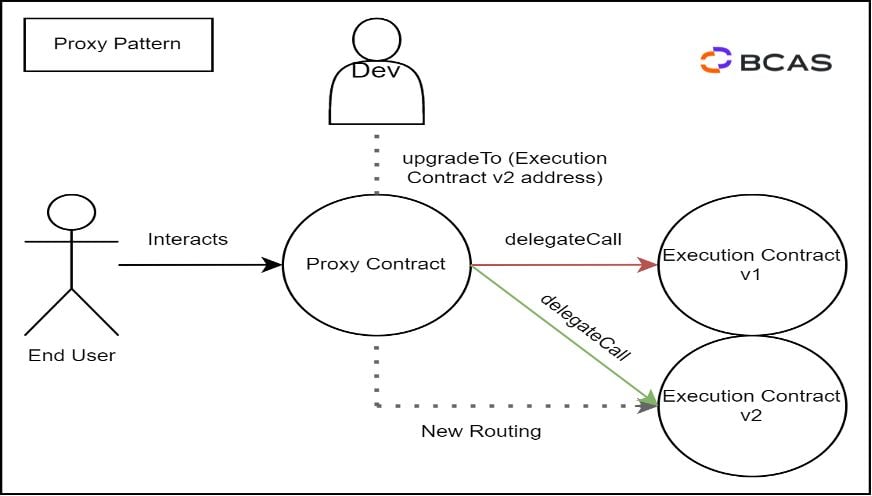
Figure 5 – Proxy Pattern Example
Initially, an external caller initiates a function call to the proxy. Subsequently, the proxy delegates the call to the implementation contract for execution. Once executed, the output is returned to the proxy, which sends it back to the original caller. Because the call is delegated using "delegatecall", the function gets executed within the proxy context. This implies that the storage space of the proxy is utilized during the function's execution24.
When initially deployed, the Proxy Pattern allows ERC-4626 vaults to issue non-transferable ERC-20 shares. It is possible to do so by rerouting calls to the ERC-20 upgradeable contract to another version of the contract without any restrictions on the transferability and without affecting the end-user interaction with the vault. If such a possibility exists, it is difficult to argue that the shares are not susceptible to being transferred between the other users and, consequently, the shares of the ERC-4626 would fall under the purview of MiCA.
3rd - Does it have a Stable Value? Electronic Money Token (EMT) and Asset-Referenced Token (ART)
An Electronic money token or e-money token "means a type of crypto-asset that purports to maintain a stable value by referencing the value of one official currency."25
An Asset-referenced token "means a type of crypto-asset that is not an electronic money token and that purports to maintain a stable value by referencing another value or right or a combination thereof, including one or more official currencies".26
The meaning of "stable value" is not conditioned to the collateral or backing to the crypto-asset value reference. This argument is substantiated by the algorithmic "stablecoins" inclusion, where regardless of the protocol mechanism, if it purports to maintain a stable value, it shall be deemed an asset-referenced or electronic-money token. Therefore, fundamentally, the crypto-asset must have a pair value with the official currency, in the case of electronic money tokens, or must maintain the asset's market value or right referenced by such token, regardless of the collateral.
On another note, issuers of asset-reference tokens shall only invest the reserve of assets in highly liquid financial instruments with minimal market, credit and concentration risk or undertakings for collective investment in transferable securities (UCITS) in accordance with the European Banking Authority (EBA) guidelines27. They shall not grant any interest in any way28.
As discussed above, the main use-case vaults relying on the ERC-4626 standard is to automatize and auto-compound the allocation of the underlying asset deposited in such vault. Therefore, the shares representing the proof of ownership of the underlying asset do not intend to maintain a stable value in reference to the asset's market value or a pair value to an official currency. They represent a stake in a strategy to increase value by providing auto-compounded interest on the deposited assets. Consequently, ERC-4626 shares do not satisfy the abovementioned conditions and arguably do not classify as an E-Money Token or Asset-Referenced Token.
4th - The Others
The final category of crypto-assets is defined through exclusion, termed as "other crypto-assets", which encompasses all crypto-assets covered by MiCA, such as:
- Automatically created as a reward for maintaining a distributed ledger or validating transactions which are not ART or EMT; and,
- Utility Tokens.
- "Governance Tokens";
- Certain "Non-Fungible Tokens" (NFTs)29;
- Any other crypto-asset which is not expressly excluded from the regulation;
Except for the first example mentioned in the "other crypto-assets" category pertaining to native blockchain/Distributed Ledger Technology crypto-assets, which normally include the likes of Bitcoin, Litecoin, Dogecoin, and so forth, the other categories mentioned by way of examples are typically issued ‘on top’ of native blockchains in the form of ‘tokens’, typically adhering to pre-determined standards. It's crucial to note that any ERC-4626 shares are minted to confirm ownership of a pool of assets. They are not generated as a reward for upkeeping a distributed ledger or verifying transactions. Thus, inferring that these shares are not comparable to such an example is logical.
The second example is utility tokens, which are "only intended to provide access to a good or a service supplied by its issuer"; utility tokens do benefit from certain exemptions under MiCA, but for the sake of strict categorization, they can be viewed as falling under the category of ‘other crypto-assets’. Firstly, assuming ERC-4626 shares are transferable, in most cases, they are not restricted to a single utility supplied by the issuer. These crypto-assets benefit from DeFi composability, where any developer may access or use infrastructure without permission and can be connected in tandem to create different protocols and products. The possibility of being a "Money LEGO" by default opens unimaginable use cases for such shares30. Secondly, such shares are proof of ownership of a deposit. They are not minted to provide access to a service or acquire a good supplied by the issuer.
The third example is "Governance Tokens"31, or crypto-assets with governance or voting features. These crypto-assets enable holders to vote on project-related matters, aligning their interests with the community and promoting decentralized decision-making. By default, ERC-4626 shares represent ownership of a vault and do not inherently grant governance rights over the underlying protocol that governs the vault. Typically, protocol governance tokens fulfil this role. However, it is not entirely out of the realm of possibility to confer voting rights to these shares, although it is not the norm.
The final example is certain "NFTs", which are NFTs that do not meet the unique & non-fungibility requirements, such as being part of large series or collections or fractioned32. The ERC-4626 shares adhere to the widely adopted ERC-20 standard, which inherently establishes their fungible and non-unique nature. It is important to note that there is no debate or ambiguity regarding their classification as NFTs. Hence, they should not be mistakenly considered or labelled as NFTs, nor should they be grouped with certain "NFTs" that do not meet the actual characteristics of being non-fungible tokens.
Nevertheless, ERC-4626 shares may be considered a "crypto-asset which is not expressly excluded from the regulation". This category captures any crypto-assets which are not classified under any other category or definition. Therefore, ERC-4626 shares are deemed as "other crypto-assets" by elimination.
The MiCA ‘Reverse Card’
While our assessment may be valid, dismissing potential stipulations that may arise from other pertinent laws, regulations, rules, and guidelines, such as MiFID II, is inadequate. The reasoning for our evaluation was based on a potentially incorrect presumption, suggesting that ERC-4626 shares, where applicable, are not considered financial instruments, deposits, or funds.
As delineated in point 4 of Article 2 of MiCA, such regulation does not apply to crypto-assets that classify as one or more of the aforementioned instruments. This implies that, in accordance with the substance-over-form approach to any instrument, it is obligatory to scrutinize each crypto-asset under the provisions of MiFID II before considering MiCA. Therefore, it's important to underscore that this article is based on interpretative arguments of the law and should be treated as such.
Conclusion
The rise of DeFi has revolutionized the financial sector, empowering users with versatile tools like vaults, which aid in optimizing investments and compounding returns. Nevertheless, each vault type carries unique characteristics and limitations, mandating scrutiny for optimal utilization. As the DeFi landscape evolves, vaults are poised to significantly impact decentralized financial operations' growth and efficiency. However, it's important to note that introducing regulatory frameworks like MiCA may pose potential challenges to these innovations, underscoring the need for compliance and adaptability within this rapidly advancing sector.
---
[1] Maia, Guilherme and Vieira dos Santos, João, MiCA and DeFi ('Proposal for a Regulation on Market in Crypto-Assets' and 'Decentralised Finance') (July 1, 2021). Forthcoming article in "Blockchain and the law: dynamics and dogmatism, current and future"; Eds: Francisco Pereira Coutinho, Martinho Lucas Pires and Bernardo Barradas, Available at SSRN: https://ssrn.com/abstract=3875355
[2] In this article, the term "derivatives" is used for technical or descriptive purposes only and does not imply a legal definition or classification as a financial instrument.
[3] Liquid Staking Derivatives is a transferable representation of a user's staked assets (on a Proof-of-Stake or similar consensus mechanism) and the yield distributed by the protocol.. https://www.coingecko.com/learn/what-is-liquid-staking-liquid-staked-derivatives-you-need-to-know
[4] https://docs.beefy.finance/products/vaults
[5] Strategies are smart contracts that determine the underlying asset, where to deploy such asset, the routing of all transactions and any automated decision, such as compounding the interest. https://docs.beefy.finance/products/strategies
[6] Most vaults use a prefix for their minted crypto-assets which should be derived by the name of the protocol or the strategy vault itself, streamlining the user experience and making it easy to recognize the different vaults within the ecosystem. In our example, we do not apply the ideal prefix since the “s” is merely derived by “staking XYZ”.
[7] https://chain.link/education-hub/what-is-yield-farming
[8] https://yearn.finance/vaults/1/0xa258C4606Ca8206D8aA700cE2143D7db854D168c
[9] For simplicity purposes, we refer to WETH as ETH.
[10] The APY is variable and susceptible to market and protocol/s conditions.
[11] https://ethereum.org/en/developers/docs/standards/
[12] The ERC-4626 interface may be used for any purpose, since it is merely an interface. For the purpose of this article, we are referencing the ERC-4626 interface for yield-bearing strategy vaults.
[13] https://ethereum.org/en/developers/docs/standards/tokens/erc-4626/
[14] https://eips.ethereum.org/EIPS/eip-4626
[15] In this article, the term "derivatives" is used for technical or descriptive purposes only and does not imply a legal definition or classification as a financial instrument
[16] Digital finance: Council adopts new rules on markets in crypto-assets (MiCA), https://www.consilium.europa.eu/en/press/press-releases/2023/05/16/digital-finance-council-adopts-new-rules-on-markets-in-crypto-assets-mica/#:~:text=The%20EU%20brings%20crypto%2Dassets,crypto%2Dassets%20(MiCA).
[17] MiCA Regulation, Article 3, number 1(5)
[18] It is essential to emphasize that the scope of this qualification is limited to the instances of the described vaults implementing the ERC-4626 interface. Please note, any conclusions or inferences drawn are specifically tied to these representative cases, and may not universally apply to other use-cases.
[19] For the scope of this article.
[20] https://github.com/centrehq/centre-tokens
[21] https://blog.chain.link/upgradable-smart-contracts/
[22] For simplicity sake, we shall neglect the SELFDESTRUCT opcode. For more information: https://hackmd.io/@vbuterin/selfdestruct
[23] The Simple Proxy Pattern, the Transparent Proxy Pattern and the UUPS Pattern. For more details: https://blog.chain.link/upgradable-smart-contracts/
[24] https://dev.to/envoy_/upgradable-erc-20-smart-contract-part-1-5433
[25] Article 3, n1, (7) MICA
[26] Article 3, n1, (7) MICA
[27] Article 38 MICA
[28] Articles 40 for ART and 50 for EMT.
[29] Which are not deemed to be unique or non-fungible.
[30] https://chain.link/education-hub/permissionless-composability
[31] While the term and specific definition of "Governance Tokens" are not explicitly outlined in MiCA, it is worth acknowledging their significance within the DeFi ecosystem. While such crypto-assets may fall under the broader category of "any other crypto-asset not expressly excluded from regulation", their influence warrants recognition and inclusion in the discussion.
[32] MiCA Preamble 10 and 11. The NFT discussion merits a separated article/discussion. For the scope of this article, no further detail will be provided.
Topic
Crypto regulation

